

The UK’s National Protective Security Authority (NPSA) and National Cyber Security Centre (NCSC) have developed the Secure Innovation campaign to help founders and leaders of innovative early-stage tech companies to protect their IP, competitive advantage, and reputation from state threat actors and state backed competitors. The campaign also aims to inform organisations of security risks, particularly those arising from state threats, to helping them to understand how to manage them. It is particularly relevant for spin-outs and start-ups with significant potential to grow.
The scheme aims is to connect organisations with KEYSIGMA’s security reviewers and assured Cyber Advisors who can review an organisations current protective security practices and provide high quality guidance and advice developed by the UK’s national technical authorities.
Free Cyber Essentials Certification
The Security Review scheme is funded through a joint initiative between the Department for Business and Trade (DBT), the Department for Science, Innovation and Technology (DSIT), National Protective Security Authority (NPSA), and the National Cyber Security Centre (NCSC). The review will provide a high-level overview of your overall protective security posture—not limited to cyber security. While cyber security remains a critical element, the review will offer a holistic view of security practices by considering the approach to: the controls listed below:







The scheme bears the majority cost of each Review through a £2,500 grant, with a supplement of £500 from each business. To encourage organisations receiving a security review to progress toward achieving Cyber Essentials certification, a £300 voucher code towards Cyber Essentials will be provided to each participating organisation.
Who is Eligible for a Part Funded Security Review?
To qualify for the funded security review, you company must:
Eligible Organisations





Eligible Industries
To be eligible to apply, organisations must be working in one of the 17 sensitive areas of the economy set out in the National Security and Investment Act, or one of the selected sectors in Invest 2035: the UK’s modern industrial strategy (Advanced Manufacturing, Clean Energy Industries, Defence, Life Sciences), as set out below:




















Click here to see details of the 17 types of notable acquisitions under NSIA.
The Secure Innovation Process
The Secure Innovation Process Consists of 6 Stages:
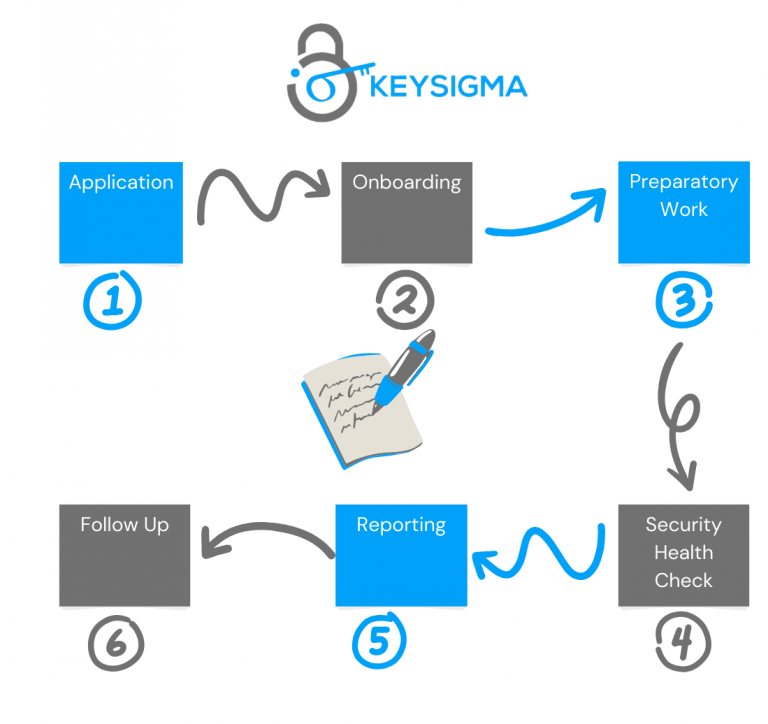
Secure Innovation Security Reviews is a subsidy scheme with participating companies will contributing £500 (Including VAT); whilst HMG will fund the remaining £2500 (Including VAT). Companies that meet the eligibility criteria and successfully pass the application process will be offered access to the partially funded Secure Innovation Security Review.
- To be accepted onto the scheme, your application must demonstrate that you are both able and willing to dedicate resources, including where necessary financial resources, to effectively implement your protective security strategy.
Your KEYSIGMA consultant will guide you through the formal application process.
Following approval of your application you will need to:
- Formally appoint KEYSIGMA as your security reviewer.
- Agree to the scheme’s terms and conditions.
- Agree to KEYSIGMA’s terms and conditions.
- Pay the £500 contribution towards the assessment.
- Arrange the site visit with your Security Reviewer.
Before the site visit takes place, you will be asked to complete the following preparatory steps:
1. Appoint Security Leadership – designate a responsible individual to oversee the organisations engagement with the Security Review process.
2. Identify Critical Assets – clearly define the assets that are most vital to your organisation’s operations, reputation and intellectual property.
3. Integrate Security Risks into Your Corporate Risk Register – ensure that relevant security threats are formally recorded and considered within the organisations broader risk management framework.
4. Complete the Foundation layer of the NCSC’s My Cyber Toolkit – this contains the most urgent actions to protect businesses from common cyber threats (specific instructions are provided for any actions not already in place). (N.B. This is a Beta service).
Cyber Essentials Voucher
To encourage participating organisations to progress towards achieving Cyber Essentials certification after their review has been completed, a £300 voucher code towards Cyber Essentials will be provided to each organisation. This funding also comes from the same HMG Fund. The voucher will be sent by Business West within your offer email.
Whilst not mandatory, KEYSIGMA strongly recommends attempting your Cyber Essentials assessment as part of the preparatory phase, as this will allow the KEYSIGMA Security Reviewer to provide tailored advice to the non compliances that your organisation has against the standard as part of the Security Review.
The KEYSIGMA security reviewer will visit your site to review your security arrangements against the Secure Innovation framework. The KEYSIGMA reviewer will use the health check questionnaire to support the engagement and will which covers the following themes:
- Protective Security Governance.
- Security Culture.
- Risk Management.
- Cyber Security.
- Secure Supply Chain and Partnerships.
- Incident Management
It is important to note, that the KEYSIGMA security reviewers delivering the scheme are not be experts in all of these areas and have much more expertise in guidance and implementation of controls relating to Cyber Essentials. The KESYIGMA reviewer will provide guidance on their areas of expertise and will provide guidance aligned with resources from the NPSA and the NCSC for areas outside of our core competencies.
Following the site visit, the KEYSIGMA Security Reviewer will compile a written report that serves as a tailored action plan for your organisation. This report will:
- Summarise the findings from the protective security health check.
- Highlight key areas for improvement.
- Provide practical recommendations. Where appropriate, the report will signpost NPSA and NCSC resources to support you in addressing the identified risks.
Before your chosen Security Reviewer submits the report, it must be signed by you to confirm you are satisfied with its contents. Alternatively, written confirmation of approval via email must be provided as evidence. Copies of the completed reports will be shared with Business West, Innovate UK, NPSA, the NCSC and the DBT and DSIT project teams for monitoring and evaluation purposes. NPSA and the NCSC may dip check a selection of these reports for consistency and quality monitoring.
Follow up Call
Six months after the initial site visit, the KEYSIGMA Security Reviewer will conduct a follow-up call with you to assess progress and identify any ongoing or emerging challenges. During this call, the KEYSIGMA Security Reviewer will complete a second Health Check Questionnaire and produce a 6-Month Follow-Up Report summarising the discussion and any developments since the initial review.
This follow-up is a key component of the overall evaluation of the Secure Innovation Security Reviews scheme. It not only helps measure the impact of the review process but also provides you with a clear understanding of remaining gaps and areas for continued improvement.
Satisfaction Surveys
Following both the site visit and the six-month check-in, you will be contacted to provide feedback on your experience of the Secure Innovation Security Review Scheme. This feedback is a vital part of the programme. By completing the feedback process, you will help us evaluate the scheme’s effectiveness, identify areas for improvement, and assess behavioural change over time.
How to Apply
Speak with us
Secure Innovation Frequently Asked Questions
The Security Review scheme provides early-stage innovative companies holistic and actionable protective security advice to support them to protect their IP, looking at the company’s approach to protective security governance, risk and incident management, security culture, cyber security, and supply chains and partnerships.
Businesses receiving a Security Review will also receive a £300 voucher towards Cyber Essentials certification. Cyber Essentials is recommended by the NCSC as the minimum baseline for cyber security in the UK.
The Security Review scheme provides early-stage innovative companies holistic and actionable protective security advice to support them to protect their IP, looking at the company’s approach to protective security governance, risk and incident management, security culture, cyber security, and supply chains and partnerships.
Businesses receiving a Security Review will also receive a £300 voucher towards Cyber Essentials certification. Cyber Essentials is recommended by the NCSC as the minimum baseline for cyber security in the UK.
To be eligible to apply:
- You must be a UK registered and trading business.
- You must be a small or medium sized enterprise (under 250 people)
- You must agree to contribute £500 (including VAT) towards the cost of the Security Review.
- You must be able and willing to dedicate resource, including potential financial resource, to developing your protective security strategy.
- You must be able and willing to complete the full review process, including the 6-month follow-up review and submission of any required documentation.
- You must be working in one of the 17 sensitive areas of the economy set out in the National Security and Investment Act, or within one of the four selected areas of the UK’s Modern Industrial Strategy (see below for further details of these sectors).
- Receipt of this support is subject to the Subsidy Control Act (2022). To qualify an enterprise cannot have received more than £315,000 Minimal Financial Assistance (MFA) and or De Minimis within any three-year period (in Northern Ireland €300,000 De Minimis).
- If your business in based in Northern Ireland, please note that EU State aid rules now only apply in limited circumstances. Please see the Windsor Framework to check if these rules apply to your organisation.
National Security and Investment Act:
- Advanced materials (including semiconductors)
- Advanced robotics
- Artificial intelligence
- Civil nuclear
- Communications
- Computing hardware
- Critical suppliers to government
- Cryptographic authentication
- Data Infrastructure
- Defence
- Energy
- Military and dual-use
- Quantum Technologies
- Satellite and space technologies
- Suppliers to the emergency services
- Synthetic biology
- Transport
UK Industrial Strategy:
- Advanced Manufacturing
- Clean Energy Industries
- Defence
- Life Sciences
To encourage organisations receiving a security review to progress toward achieving Cyber Essentials certification (the NCSC recommends Cyber Essentials as the minimum standard of cyber security for all organisations), a £300 voucher code towards Cyber Essentials will be provided to each organisation after the report has been submitted. This voucher code will be sent with your successful application email.
The voucher code can be redeemable against certifying or recertifying to CE level 1 (independently verified self-assessment). Organisations wishing to use this must do so by 31st March 2026.
This voucher code is non-transferable and may only be used by the organisation to which it was issued.
Secure Innovation Security Review participating businesses contribute £500 towards the service, with the remaining £2,500 funded by the scheme.
On acceptance participating businesses will receive a £300 voucher towards cyber essentials certification.
State threats are overt or covert actions by foreign governments which fall short of direct armed conflict with the UK but go beyond peaceful diplomacy and expected statecraft to harm or threaten the safety or interests of the UK or our allies.
State threats present a real and evolving risk to the UK. They can manifest in a range of forms. These include attempts to:
- steal sensitive information through espionage or cyber attacks
- threaten the public’s safety, including through physical violence.
- harm our prosperity
- undermine our values and freedoms
State threats do not only materialise against government and intelligence agencies. Some states are particularly interested in industrial or commercial information which could be used to support their own economy or military. This information may not be “classified” or an obvious target for espionage.
States may seek to exploit foreign direct investment, academic partnerships and supply chains to gain access to sensitive information.
This includes information on companies’ products and plans or commercial/academic research. State actors could seek to fast track their own technological capabilities or increase their military advantage. Examples of industries in which states show particular interest include advanced materials, biotech, and artificial intelligence. It also includes research and mainly academic research, particularly in STEM (science, technology, engineering and mathematics), dual-use technologies, emerging technology and other commercially sensitive areas. As with business information, state actors could seek to exploit research to improve their own technological or military capabilities.
Yes. State actors do not only target large corporations or government entities. In fact, companies of all sizes —especially those with lower levels of security—can be attractive targets.
No business is too small or too early-stage to be of interest, particularly if it holds valuable intellectual property, innovative technologies, or sensitive data.
Yes. There are steps businesses of any size can take to reduce their vulnerabilities to state threats. The aim of the protective security measures outlined in Secure Innovation is to reduce the risk to the business and increase the risk to the state actor trying to get hold of their assets. The better an organisation’s protective security measures are, the harder a state actor will have to try to get access to their technologies, and the greater the chance that they will be detected doing so. State actors will make a risk-benefit decision on who to target, so the higher the risk to them, the less likely they are to try
Secure Innovation Security Reviews is a subsidy scheme. Until all slots are filled, organisations that meet the eligibility criteria and successfully pass the application process will be offered access to a partially funded Secure Innovation Security Review. Participating companies will contribute £500; while the government will fund the remaining £2,500.
Funding for the scheme is limited and will be awarded on a first-come, first-served basis. Once the available funding has been allocated, no further awards can be made—meaning only a limited number of companies will be able to benefit from the scheme this financial year.
It should be noted that the government will fund £2,500 (including VAT) of the total cost of the review which is £3,000 (including VAT); by making an application for a Security Review an organisation is confirming their agreement to fund the remaining £500 (including VAT) of the overall cost. This will be invoiced and paid directly to the Security Reviewer.
KEYSIGMA are approved Security Reviewers due to our NCSC assured Cyber Advisory status.
We have applied to be part of this scheme, have completed training on the Secure Innovation Security Review framework with NPSA and NCSC and passed a knowledge check to demonstrate an understanding of the scheme and framework, and have committed to completing reviews anywhere in the UK.
- Complete the KEYSIGMA Secure Innovation Security Review Application Form by contacting info@keysigma.co.uk.
- Complete the Innovate UK Business Growth Consortium’s application form.
- Accept the scheme’s terms and conditions.
- Formally appoint KEYSIGMA as their Security Reviewer.
- Paying the outstanding £500 to KEYSIGMA.
- Complete the preparatory work.
- Arrange an in-person site visit with the KEYSIGMA.
- Review and sign-off the report.
- Confirm that your Security Reviewer has submitted the final report and their invoice for £2,500 via email to secureinnovation@iukbg.ukri.org.
If you require an extension, should contact KEYSIGMA at info@keysigma.co.uk as soon as possible, who will try to arrange an extension with the Secure Innovation scheme’s owners.
If the report is not submitted within the time allowed and an extension has not been agreed; or if an extension has been agreed, but the report is not submitted before the expiry of the extension period, the scheme’s owners will assume the review report is not going to be submitted and withdraw the funding offer.
Firstly, you should share the content of your confirmation email along with a copy of your application form with the appointed security reviewer.
Secondly, you should undertake the Secure Innovation Action plan preparatory work.
Yes. It will only be shared with selected individuals within DBT/DSIT, Innovate UK, NPSA and the NCSC.
No, the £3000 is for the purposes of the security review only.
Applications for the current scheme will be open until the end of the 25/26 financial year. There are grants available for 500 organisations, which will be allocated on a first-come-first-served basis to organisations who pass the eligibility criteria and assessment.
This is not a certification scheme, as there is no requirement and/or test or audit to ensure organisations have implemented the security measures recommended by the review.
The scheme does not offer a logo which companies can display to show they have gone through the process. This is to avoid the risk of the scheme being misinterpreted as a certification or accreditation scheme. However, you can mention having had a security review completed as a way of demonstrating your commitment to security.
Data will be collected through various stages of the scheme, including the application process, site visit, written report, Health Check Questionnaires, and feedback surveys. This may include business contact details, security-related information, and feedback on the scheme.
Your data will be shared with the following organisations involved in the funding, delivery and oversight of the scheme:
- Department for Business and Trade (DBT)
- Department for Science, Innovation and Technology (DSIT)
- Innovate UK
- National Protective Security Authority (NPSA)
- National Cyber Security Centre (NCSC)
- Innovate UK Business Growth service consortium delivery partner
These organisations are responsible for funding, managing, delivering, and evaluating the scheme. Data sharing enables them to monitor the scheme’s effectiveness, assess behavioural change, and inform future improvements or expansion.
National Protective Security Authority (NPSA) are part of MI5. They are the UK’s national technical authority for personnel and physical security. Their mission is to reduce the vulnerability of UK government, businesses, and academia to a range of threats, including terrorism, espionage, and sabotage. NPSA provides expert guidance to help organisations strengthen their protective security posture.
The National Cyber Security Centre (NCSC) are part of GCHQ. They are the UK’s national technical authority for cyber security. Their role is to make the UK the safest place to live and work online. They support the most critical organisations in the UK, the wider public sector, industry, SMEs as well as the general public.
No. Your data will not be used for marketing purposes unless you have explicitly consented to this.
In accordance with the UK General Data Protection Regulation (GDPR) and the Data Protection Act 2018 (as applicable), by participating in the Secure Innovation Security Review Scheme, you acknowledge and agree that any data you provide or that is collected throughout the scheme via the site visit, written report, Health Check Questionnaires, and feedback surveys—may be shared with Innovate UK Business Growth service consortium delivery partner, the Department for Business and Trade (DBT), the Department for Science, Innovation and Technology (DSIT), the National Protective Security Authority (NPSA), and the National Cyber Security Centre (NCSC). This data will be used solely for the purposes of administering, evaluating, and improving the scheme, and for monitoring its impact. All data will be handled in accordance with applicable data protection laws and will not be used for marketing purposes without your explicit consent.
By providing your contact details, you agree to any partner mentioned above storing your information and they may contact you at a future date to learn about your experiences and to share opportunities related to other Secure Innovation products. Your data will be handled in accordance with the relevant privacy notices of each organisation as available on their websites.
If you have any questions or concerns about how your data is being used, you should contact KEYSIGMA at info@keysigma.co.uk or the data protection officer for the scheme at secureinnovation@iukbg.ukri.org
Previous Participant Feedback











